UC4.2 – Truck low-speed connected perception cyber-security
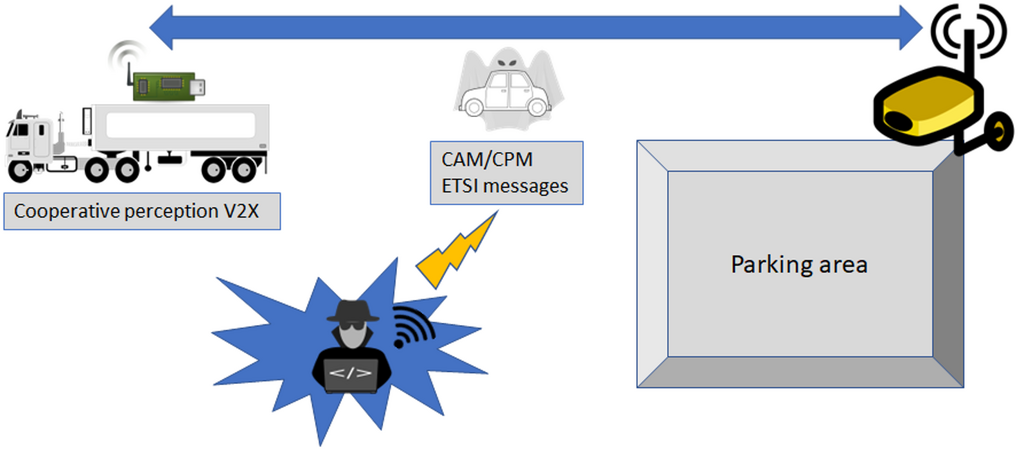
In Use Case 4.2, the SUNRISE SAF is tested for truck low-speed connected perception cyber-testing. The SUT is a connected perception AD subsystem that is compromised by cyber-security threats. The main aim is to combine in a simulation environment several aspects simultaneously (physical environment, perception, V2X connectivity) and study the effects of physical or remotely executed cyber threats on collective environment awareness.
There are two functional scenarios defined from T7.1 for assessing the connected perception cyber-security performance in use case 4.2. The first is the “distorted camera input” scenario, whereas the second one is the “CPM message attacked” scenario.
Use case overview
UC4.2 builds on top of the CCAM system of UC4.1 and the perception system of UC1.3, and deals with a connected perception AD subsystem that is compromised by cyber-security attacks.
Objectives
In virtual simulation, combine several aspects simultaneously (environment, perception, V2X connectivity, cyber-attacks) and study the effects of remotely executed cyber attacks on collective environment awareness.
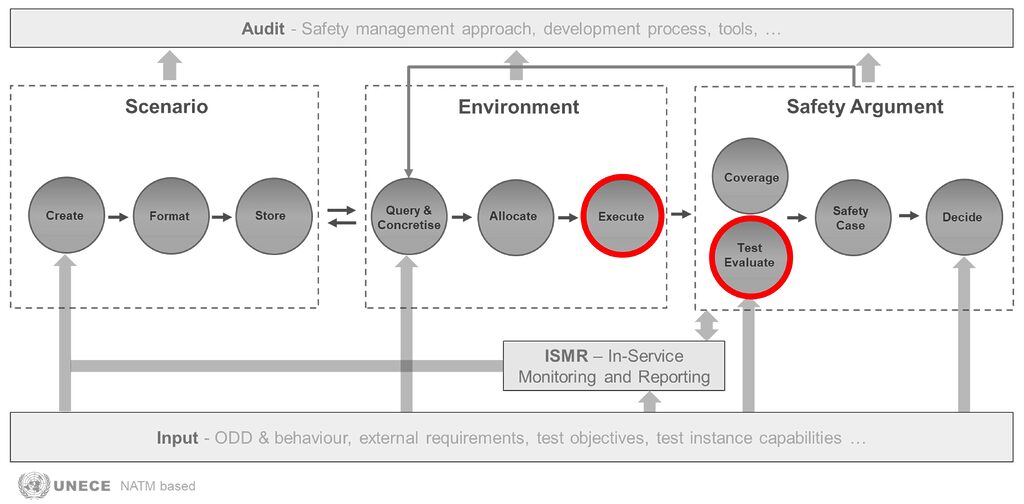
SAF blocks demonstrated
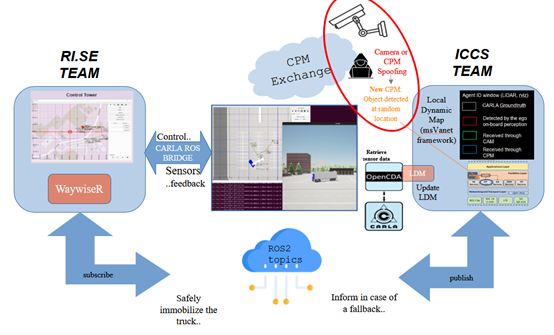
Safety case setup
Two partners spoof the Road Side Unit (RSU) camera and falsify CPMs while controlling a virtual truck in a parking manoeuvre in a CARLA-ns3 co-simulation environment. A virtual camera-based RSU module is assumed to provide information about the scene through CPMs (as standardized by ETSI). Considered pass/fail criteria are similar to the truck parking system of UC4.1, however additional Key Performance Indicators (KPIs) related to the effects of the cyber attack have been defined.
Test environments
This UC did not focus on covering multiple test scenarios as this is already addressed by the work in UC1.3 (Collective Perception testing).
Although in this SAF demonstration we mainly focused on the execute part and test evaluate part and not on scenario space coverage, CARLA-ns3 co-simulation framework as implemented by this UC, allows to parameterize network/message exchange characteristics and hence creating variations of the same concrete scenario for different CAM/CPM propagation loss rates among any connected agents. Therefore, the work performed here (CARLA-V2X co-simulation) is considered an important step towards studying in simulation these types of scenarios and we believe it will be a valuable tool for Threat Analysis and Risk Assessment (TARA) experts, enabling them to build, visualise, and analyse the attacker’s behaviour and operations to better understand the potential impacts of cyberattacks. This will in turn allow for quantification of different qualitative parameters set currently by experts when performing TARA analysis making attack feasibility assessment more objective and not solely based on experts’ opinions and experience.
In this UC a real-world attack is assumed but without directly attacking the vehicle under test but the infrastructure or the V2X message. It is acknowledged that these kinds of attacks are neither solely a cybersecurity nor a SOTIF topic. This should be considered as a cross-domain safety/security topic that requires a combined threat and risk analysis by the AV/CCAM engineers. The risk stemming from objects reported by external sources is considered by the recent cybersecurity standards. It is important that mitigations are evaluated, both inside and outside the vehicle [see ISO/SAE 21434, 8.9, RQ-08- 12 (risk transfer)]. CCAM systems cybersecurity extends to systems outside the CAV and hence it is a more complex task since typical cybersecurity measures like integrity checks or proofing the authenticity as the attacked environment is not cyber-physically connected to the considered system.
Test scenarios selected
The test scenario was one of the reverse parking scenario applied in UC4.1 augmented by the event of a falsified CPM reception by the truck leading to interruption of the parking maneuver.
Key take aways
‘Execute’ sub-block:
‘Test’ evaluate sub-block:
